1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
| #include<iostream>
#include<string>
using namespace std;
char message[] = { 0xD1,0x37,0xd9,0x5b,0xf0,0xA2,0x32,0xC6,0x30,0xA7,0x8C,0x50,0x7E,0x3E,0xA7,0x3A,0xBA,0xC0,0x58,0x6b,0x81,0x85,0x6b,0x1c,
0x4c,0xf5,0x80,0x7c,0x8a,0xC1,0x42,0x97,0x90,0xc7};
char v14[264] = { 0 };
char v3 = 0;
char v7 = 0;
int v11 = 0;
char v6 = 0;
int v10 = 0;
int v12 = 0;
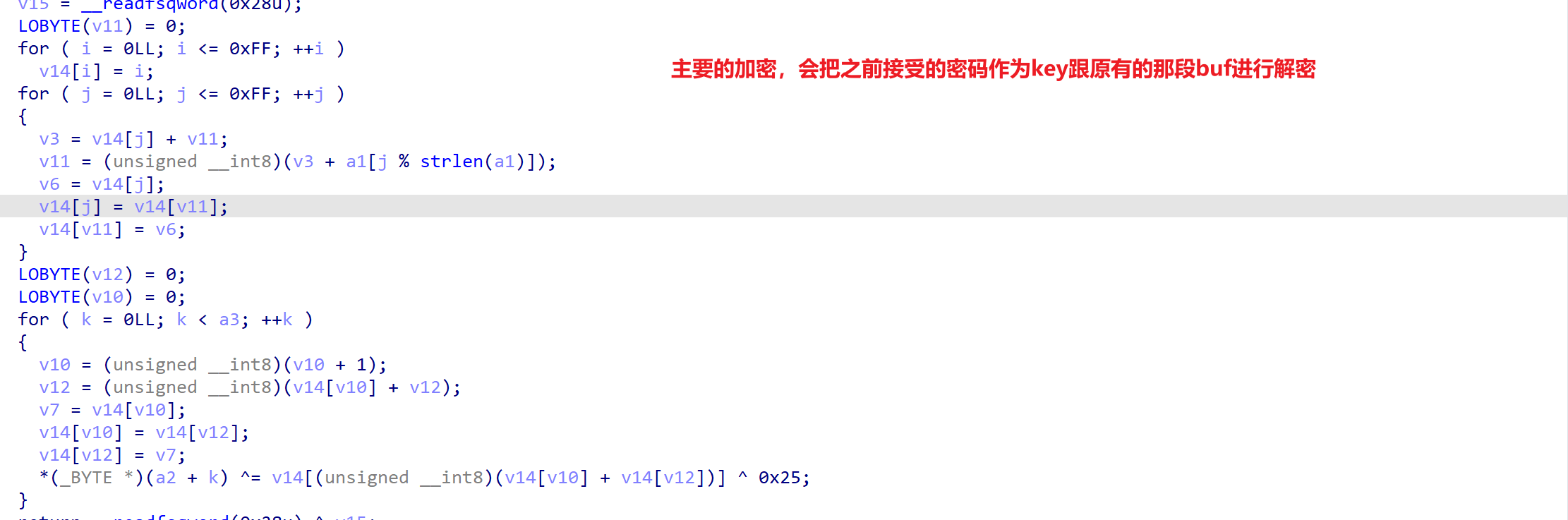
int encryption(const char* buf,char* message,int length) {
for (int i = 0; i <= 0xFF; ++i)
v14[i] = i;
for (int j = 0; j <= 0xFF; ++j) {
v3 = v14[j] + v11;
v11 = (unsigned __int8)(v3 + buf[j % strlen(buf)]);
v6 = v14[j];
v14[j] = v14[v11];
v14[v11] = v6;
}
for (int k = 0; k < length; ++k) {
v10 = (unsigned __int8)(v10 + 1);
v12 = (unsigned __int8)(v14[v10] + v12);
v7 = v14[v10];
v14[v10] = v14[v12];
v14[v12] = v7;
*(char*)(message + k) ^= v14[(unsigned __int8)(v14[v10] + v14[v12])] ^0x25;
}
return 0;
}
int main() {
encryption("WangDingCUPKEY!!", message, 0x22);
for (int i = 0; i < 34; ++i) {
printf("%c", message[i]);
}
}
|